Contents:
Software product development for healthcare requires keeping HIPAA regulations in mind to avoid penalties, gain patient trust, and comply with regulations. In 2023, over 540 organizations reported health data breaches to the HHS Office for Civil Rights (OCR), affecting beyond 112 million people, compared to 590 organizations and 48.6 million impacted individuals in 2022. This indicates growing risks for companies working in the healthcare industry.
Our guide will help you get a HIPAA compliance checklist for software development to update or create a reliable application with all practices in mind. We share insights and practical tips from our 15+ years of healthcare app development experience and will help you understand what you should pay attention to while working on your product.
HIPAA Compliance Software Requirements for 2026: 5 Main Rules
Healthcare application development compliance requires the protection of the privacy and integrity of your patients’ PHI during storage, transmission, and access. This includes the following 4 basic HIPAA rules that define administrative, technical, and physical safeguards.
1. Privacy Rule
The Privacy Rule defines ePHI and outlines the rights patients have over their health information. This rule applies to all identifiable health data, including records related to physical & mental health, treatments, and payments. It significantly limits how these records can be shared.
Healthcare software that handles PHI and ePHI must ensure the following:
- Patient access to data: patients must be able to access, inspect, and request copies of their PHI
- Restricted disclosure: PHI can only be shared under narrow legal, care, or research circumstances
- Obtaining consent: disclosures require patient consent
- Designated privacy officer: a privacy officer must oversee compliance and ensure that written privacy policies are implemented
- Procedures for third-party sharing: PHI disclosures to business associates or third parties must follow strict protocols
Complying with these features allows organizations to avoid HIPAA violations and build patients’ trust in the healthcare system.
2. Security Rule
While the Privacy Rule focuses on who can access PHI, the Security Rule ensures that PHI remains protected from breaches and unauthorized access. This rule sets technical, physical, and administrative guidelines to protect ePHI across all systems.
Key administrative measures:
- Risk assessments: conduct regular analyses to identify security vulnerabilities
- Access control policies: restrict access to ePHI based on role and job function
- Workforce training: all employees must receive training on security practices and incident response procedures
Key physical measures:
- Secure premises: ensure that only authorized personnel can access physical systems storing ePHI (servers, computers, etc.)
- Device security: establish procedures for secure use, disposal, or reuse of devices that store ePHI
Key technical measures:
- Data encryption: encrypt ePHI during storage & transmission to protect it from unauthorized access
- Access controls: use multifactor authentication to prevent unauthorized access
- Activity monitoring: implement systems to track and log all access attempts, helping detect potential security breaches
Following this checklist for the Security Rule will help you ensure sensitive health information remains protected while maintaining functionality for healthcare providers and patients.
3. Breach Notification Rule
Breaches can happen even with the best practices in place for health data security applied. The Breach Notification Rule outlines the steps organizations must take if a breach of unsecured PHI happens.
This is your checklist for the Breach Notification Rule:
- Notify affected patients: they must receive written notification (via mail or email) within 60 days of discovering the breach
- Public and media alerts: for breaches affecting 500+ individuals, the organization must notify the media and issue a public announcement
- Report to HHS: breaches involving 500+ individuals must be reported to the Department of Health and Human Services immediately, while smaller breaches can be reported annually
- Vendor notifications: business associates must notify covered entities of breaches, following the same timelines
This rule provides transparency and ensures patients are aware of what’s going on with their data.
4. Omnibus Rule
The Omnibus Rule defines how violations of the HIPAA Privacy and Security Rules are investigated and penalized. It provides a framework for auditing, monitoring compliance, and applying penalties when violations occur.
Here’s how the Omnibus Rule works:
- Audits and risk assessments: organizations must conduct regular audits to identify compliance gaps
- Corrective actions: when non-compliance is identified, organizations must implement corrective action plans to address the issues
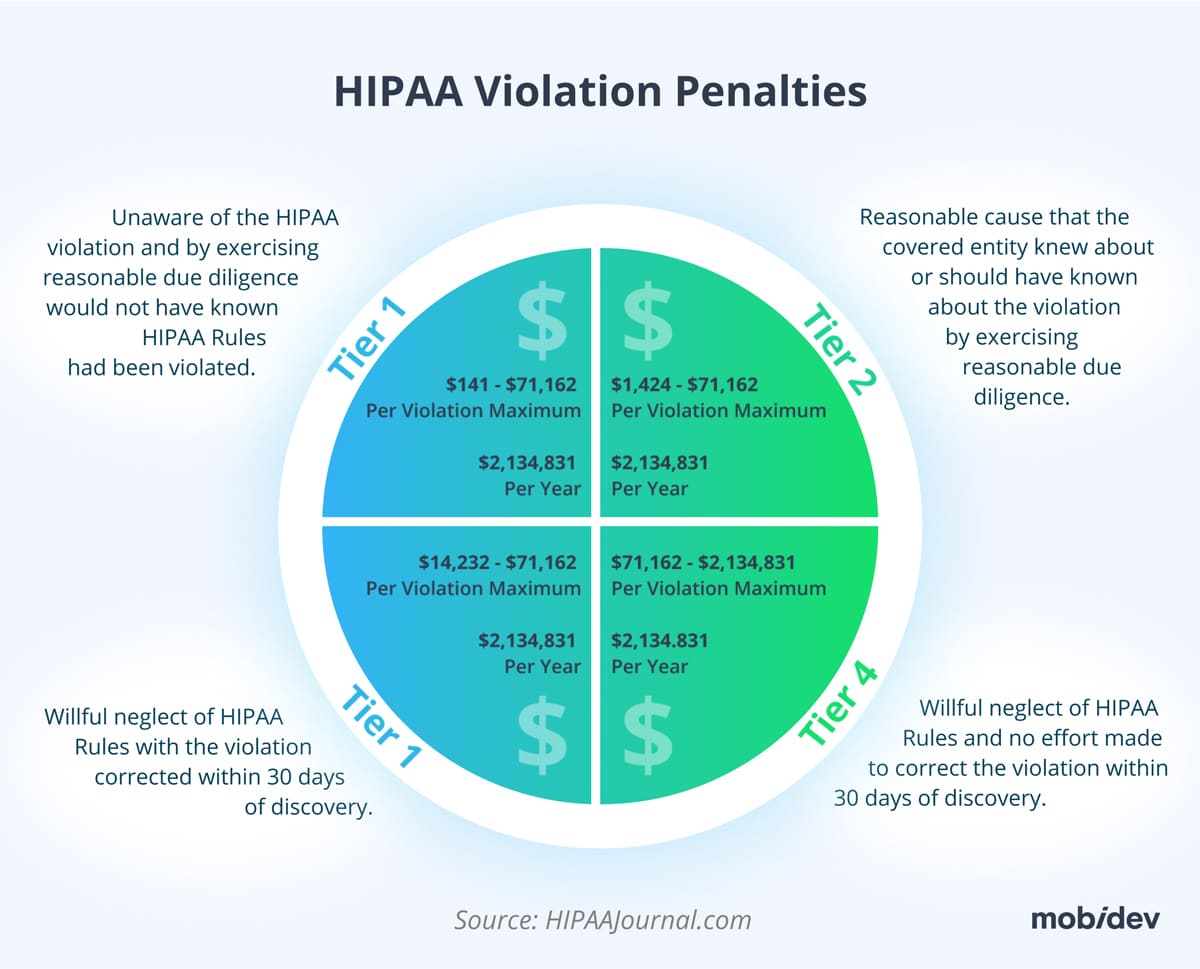
- Fines and penalties: the severity of penalties depends on the level of negligence, with fines increasing for more severe & repeated violations
- Business associate accountability: covered entities are responsible for ensuring their business associates follow HIPAA rules, as any violations on the associate’s part can result in penalties for the covered entity
The Omnibus Rule ensures organizations remain diligent in maintaining compliance by holding them accountable for breaches or violations.
5. Enforcement Rule
The Enforcement Rule establishes the protocols and penalties for violations of HIPAA’s Privacy, Security, and Breach Notification rules by covered entities and business associates.
The key points of the Enforcement Rule are:
- Application of HIPAA privacy and security rules: ensures all covered entities and business associates must uphold HIPAA requirements in protecting PHI and ePHI
- Mandatory breach reporting: requires any breach of unsecured PHI to be reported to affected individuals, the Department of Health and Human Services and, in certain cases, the media
- Disclosure and marketing restrictions: sets limits on the use of PHI for marketing or sales without explicit patient authorization and mandates accounting for disclosures of PHI
- Contracts for business associates: BAAs must include specific clauses that enforce HIPAA’s security standards, protecting ePHI during any transfer or processing by third parties
- Civil and criminal penalties: the rule introduces a tiered penalty structure based on the level of negligence, imposing fines and sanctions on entities failing to comply with HIPAA’s requirements
HIPAA Updates and Changes Effected in 2024
While key features remain the same, HIPAA compliance software requirements are regularly updated for better protection. This requires you to apply all changes when creating a new healthcare application or modernizing outdated medical software. Below you’ll find the latest proposals and approved updates of the HIPAA regulation.
1. HIPAA Privacy Rule Proposed Changes:
- Reduce time for providing PHI from 30 days to 15 days
- Allow patients to inspect PHI in person and take notes or photographs
- Expand use/disclosure permissions for health and safety threats
- Eliminate the requirement for written acknowledgments of privacy notices
- Introduce a fee structure and estimates for PHI requests on websites
2. Part 2 and HIPAA Alignment:
- Simplified consent for future disclosures of SUD records for various purposes
- Authorization for redisclosure of SUD records under HIPAA Privacy Rule
- Expansion of patient rights regarding the use/disclosure of their SUD records
3. Reproductive Health Care Privacy Enhancements:
- 3. Prohibit the use or disclosure of PHI for conducting any criminal, civil, or administrative investigations or proceedings related to reproductive health care
- Introduce a requirement for entities requesting PHI related to reproductive health care to sign an attestation confirming the information will not be used for prohibited purposes
4. Proposed HIPAA Security Rule Updates:
- Introduction of sector-specific cybersecurity performance goals (CPGs)
- Anticipated mandatory adoption of some cybersecurity measures
5. HIPAA Compliance and Enforcement:
- Potential increase in civil monetary penalties for HIPAA violations
- Continued focus on providing guidance rather than rule changes for some compliance issues
6. General HIPAA Compliance Adjustments:
- Update requirements for how covered entities inform patients about their privacy practices, potentially eliminating the need for patients to acknowledge receipt
- Expand the definition of electronic health records to include billing information, requiring that these records also be accessible to patients upon request
7. Ongoing and Future Considerations:
- Monitor the Federal Register for the publication of final rules which will solidify the proposed changes into enforceable requirements
- Expect new rules to standardize electronic signatures and potentially adjust requirements for healthcare transactions to improve efficiency and security
While many new rules are still simply proposals, they are likely to be accepted. That’s why it’s best for you to constantly monitor HIPAA technology requirements and collaborate with developers who can quickly implement any changes.
7 Steps to Make Your Healthcare App HIPAA-compliant for 2026
Follow this HIPAA compliance software checklist to create and improve applications in the healthcare industry. We cover the fundamental encryption requirements and provide a step-by-step guide to full compliance.
1. Set up HIPAA Encryption Requirements
Focusing on HIPAA-compliant software development requires you to use these encryption approaches:
- Full disk encryption (FDE) – secures entire storage devices using encryption algorithms like AES, protecting the operating system, applications, and user data
- Virtual disk encryption (VDE) – protects data on virtual disks within cloud systems, allowing encryption of specific virtual environments with unique keys
- File & folder encryption – encrypts specific files or folders using AES, allowing sensitive information to remain secure and unreadable without the correct decryption key
This ensures your website, application, and software in general remain completely protected from all sides.
2. Establish Transport Encryption
It’s necessary to encrypt all ePHI before transmission. HIPAA-compliant software uses SSL and HTTPS protocols as the first step to protecting sensitive health data. Also, cloud providers should support custom SSL configurations to ensure strong encryption methods according to the HIPAA-compliant hosting checklist. It protects all pages that collect and show health data: dashboards, login pages, etc.
MobiDev’s team recommends validating whether the HTTPS protocol is set up properly and whether your TLS versions are up-to-date or not.
Additionally, passwords should be hashed and stored securely to prevent compromise. Combine them with a requirement to set up complex passwords with special symbols and you’ll get maximum security. If your solution is WordPress-based, check out this HIPAA-compliance checklist for WordPress websites.
3. Implement Backup & Storage Encryption
Backups are necessary to maintain continuity and prevent data loss. This feature is supported by most hosting providers. However, it’s important to ensure data is stored securely and accessible only to authorized staff.
We recommend using AES-256 or RSA algorithms to encrypt databases, backups, logs, and all sensitive data. An alternative could be using a PostgreSQL manager with a built-in data encryption feature.
If you store data in public cloud environments like Amazon RDS or Google Cloud SQL, it must remain encrypted and inaccessible even when hosted outside your organization’s control.
4. Provide Secure Identity & Access Management (IAM)
Strong IAM policies are required to maintain HIPAA compliance. This means that institutional data, passwords, and user IDs must be as secure as possible and never shared among employees. The regulation is strict and requires maximum security for data privacy and protection.
There are some key elements to consider:
- System logs: they are required by HIPAA. The system should write access logs and event logs to track all login attempts and changes made to PHI.
- 2FA: two-factor authentication should be used to ensure only authorized users can access sensitive data and information.
- Single-sign on: use SSO to maintain security while providing data on demand. It allows users to sign in once and access a network of applications & services without having to sign in again. It’s perfect for healthcare application development when there’s a need to combine multiple apps securely.
- Biometrics authentication solutions: using fingerprints, face, or voice to access data is one of the best security measures. However, you’ll need advanced anti-spoofing techniques to prevent data theft. This can include liveness detection or multimodal authentication, supported by HIPAA.
- Artificial intelligence: AI is one of the most trending technologies in the IT and custom software development sectors, presenting numerous use cases for ensuring AI HIPAA compliance. These include monitoring patient data access, detecting potential security breaches, and promoting secure data handling practices to safeguard sensitive health information. However, it is important to ensure the security of patient data when working with third-party AI services.
- Attribute-based access control: simplifies user role management, allowing dynamic and contextual access to various locations, apps, and other resources based on attributes instead of users & actions. It’s perfect for changing structural rules over time.
Following these fundamental HIPAA software requirements will help you avoid data theft and set up multiple security layers on all stages.
5. Ensure Data Integrity
All collected, stored, and transferred information must be protected from being damaged or altered in any way. This includes both intentional and unintentional occurrences.
How do you ensure this? Start by implementing features that allow the system to immediately detect and report any unauthorized data tampering, even if just a single element has changed.
Our web application development approach achieves this by digitally signing and then verifying every piece of data stored or transmitted in the system, using PGP, SSL, and others. The whole system must be designed and built in a way that prevents any unauthorized access to the data.
Maintaining integrity and remaining HIPAA-compliance requires you to combine backups, encryption, access authorization with proper user roles and privileges, restriction to physical access to infrastructure, and many other elements.
6. Enable Data Disposal
Although there aren’t clear retention periods for data, you must adopt data retention policies that include secure disposal methods for expired data, backups, and decryption keys. You must expect that every location where data is transmitted might be making backups or copying it.
Whenever you stop using a server, the data must be disposed of as well to ensure healthcare data security and HIPAA compliance. This will help you eliminate security risks.
7. Business Associate Agreement
All third-party vendors handling ePHI must sign BAAs to ensure compliance with HIPAA regulations. Alternatively, you can host data on secure in-house servers as most providers aren’t familiar with HIPAA regulations. They might not be willing to run any risks signing this agreement, which might contradict their own business processes.
We recommend healthcare organizations to use cloud storage at the most trusted HIPAA-compliant providers*, such as:
* !! Please be aware that Apple’s iCloud is not HIPAA-compliant !!
Signing a Business Associate Agreement must concern every vendor that deals with your sensitive health data for ongoing compliance with all regulations.
HIPAA Compliance for AI applications in healthcare
AI use in healthcare is not HIPAA-compliant by default due to the way it collects, stores, and processes large volumes of sensitive health data. Developers and vendors of LLMs can be subject to HIPAA when they process protected health information on behalf of the HIPAA-covered entities, becoming business associates under this regulation.
The key risks during HIPAA compliance application development with AI are:
- Data privacy and usage: AI systems need access to large datasets, which can complicate compliance if not properly de-identified or encrypted.
- Transparency issues: many AI models are “black boxes,” making it difficult to trace how they use PHI, which could conflict with HIPAA’s transparency and accountability standards.
- Vendor management: AI solutions often involve third-party providers. These vendors must sign BAAs and follow HIPAA regulations, creating additional compliance burdens.
Here’s how you can mitigate AI risks to comply with HIPAA:
- Anonymize data before using it in AI models
- Apply clear data governance policies
- Work only with AI providers willing to sign a BAA
Basically, you must involve all the aforementioned steps with encryption and IAM policies to prevent potential fines and remain compliant.
HIPAA Compliance Software Checklist
Achieving HIPAA compliance impacts both the technical infrastructure and operational workflows of your organization. It requires continuous alignment between data security practices, employee responsibilities, and third-party vendor management.
MobiDev’s experts recommend that your Privacy Officer and each Security Officer develop their own HIPAA compliance checklist to address unique challenges in the workflow. Below you’ll find a typical checklist developed by our team to cover most cases in the healthcare industry.
Download 8-Step HIPAA Compliance Checklist
DownloadMobiDev Success Stories For HIPAA-Compliant App Development
Now that we are done with the theory, let me share some cases from MobiDev’s experience. Here you’ll find how we helped our clients achieve their business goals and innovate while ensuring HIPAA compliance.
SUCCESS STORY#1. CROSS-PLATFORM MANAGEMENT SOLUTION FOR A US-BASED HEALTHCARE ENTERPRISE
THE GOAL
MobiDev’s team was asked to create a cross-platform healthcare mobile and web application. The objective was to integrate patient-doctor interactions and allow them to exchange data. To do this, our team found a balance between speed and compatibility using native-like features, HealthKit/GoogleHealth integrations, live chat, and more. Being a complex app, it allowed for the analysis and management of information on a large scale useful for hospitals. This enabled it to be integrated with EHR.
DEVELOPMENT
The app was needed to fulfill two primary functions: a portal for patients and doctors and a management and analytics module, as well as hospital-level integration. To help achieve this goal, the client’s in-house team was involved with the development of integrations and database management.
While our team worked on a test and anonymized data, the client’s team worked on bridging and provided MobiDev with the data structure. Synchronization between our teams was essential in order to create a reliable solution that would work with different Electronic Health Records (EHR).
THE TECHNOLOGIES
Amazon Cloud Services (HIPAA compliant) were utilized in order to make the app reliable and secure. Although it was useful in this case, some hospitals are more interested in using local servers for data storage and operation. We worked with their support teams to ensure that the app fits their needs. In order to secure the data on Amazon’s web servers, our team utilized encrypted RDS.
In addition, data transportation and event management needed protection. MobiDev’s team utilized Encrypted ElastiCache to respond to this problem. Also, front-end security features were added such as cache restrictions for browsers. This prevents users from saving cached images of X-ray scans.
Search history was also restricted for browsers to prevent personal patient data from being saved like names and emails. Oauth2 and JSON Web Token (JWT) were also used to protect user authentication.
RELATED SERVICES
The following MobiDev’s services were applied in this case study. Follow the links below if you want to learn more about how to leverage our expertise for your healthcare product development.

Read full success story:
HIPAA-compliant AI-driven healthcare management solutionSUCCESS STORY#2. MEDICAL SEARCH ENGINE APPLICATION
THE GOAL
The client was looking to create the app, which is a medical search engine for patients based on a database of medical content and a website. This app is aimed at simplifying fast searches on the go and convenient offline access within an intuitive and highly responsive application.
DEVELOPMENT
In cooperation with the client, we’ve made a decision to build a native iOS app, and then proceed to Android as a separate project.
When it comes to medical apps and legally protected HIPAA-compliant software development, the quality of software products and information security are even more important. The client’s product must provide relevant and accurate information to users and must do so in a reliable and fast manner. The risks of a user failing to find and access the needed information must be minimized. We managed to build such a product and publish it on the App Store within the expected timeframe, much to the client’s satisfaction.
THE TECHNOLOGIES
The project was developed as a simple method for healthcare professionals and patients to access the most relevant medical information from a wide range of sources. Among the applied technologies were: CoreData, AFNetworking, Custom View Controls from Cocoa Controls, ViewDeckController, and JSONModel.
RELATED SERVICES
Learn more about MobiDev’s services applied in this case study. Visit the pages below if you want to learn more on how to leverage our expertise for your healthcare product development.

Read full success story:
Medical Search Engine App DevelopmentSUCCESS STORYE#3. CLOUD PLATFORM FOR GROUP THERAPY AND WELLNESS
THE GOAL
The project aimed to help people find a way of improving their well-being through evidence-based treatment, connection, support, and validation. The app provides group therapy – treatment for both mental and social health and a modality of behavioral healthcare proven as effective as individual therapy. The MobiDev team was asked to take part in the project.
DEVELOPMENT
Tracking a member’s behavioral health symptoms was among the key features to be delivered, so we developed a comprehensive measurement, monitoring, and analytics system for the app. The profound logic we’ve implemented provides in-depth analytics represented in an easy-to-get format.
The app processes and stores personal health data, so taking HIPAA requirements into account was extremely important. Collaborative work with the client’s in-house team allowed us to reach this goal.
We created a development strategy that combined open-source tools and libraries with custom development to optimize timelines and costs. Calendar, video chat, and UX were all leveraged from easily available market solutions.
Since engaging both members and clinicians was core to the platform design, we’ve thoroughly worked on UX & UI design to make an app easy to use, especially for new customers.
THE TECHNOLOGIES
Among the applied technologies were: NodeJS, NestJS, PostgreSQL, RDS, ReactJS, Ant design library, React Admin, Recharts.JS, AWS, Stripe payment integration, Google Calendar API, Amazon S3, Amazon SES, Agile management framework.
RELATED SERVICES
Learn more about MobiDev’s services applied in this case study. Visit the pages below if you want to learn more about how to leverage our expertise for your healthcare product development.

Read full case study:
Cloud Platform for Group Therapy and WellnessHow to Become HIPAA-compliant with MobiDev
MobiDev’s team has helped hundreds of clients develop and update HIPAA-compliant software since 2009. Combining consulting & engineering services we have all the capabilities to meet your specific product needs. Our healthtech experts constantly monitor HIPAA’s requirements to build high-quality software that complies with all adjacent regulations.
We can implement all development on our side or provide staff augmentation services for your in-house team, supporting you with industry-relevant expertise. Check out our healthcare app development services to learn more about our experience and contact us to discuss your product needs!