Contents:
MobiDev has been developing mobile applications since 2009, so we’ve had time to be convinced that security can either contribute to the success or lead to the failure of a mobile app. Moreover, this is true for both new and existing apps.
In this article, we’ll explain why mobile application security is coming to the forefront in 2026 while overviewing the key vulnerabilities, security standards and best practices. We’ll also walk you through practical examples of secure mobile application development and provide you with a security checklist you can use for your product.
The Importance of Mobile Application Security in 2026
The importance of mobile application security is difficult to overestimate. If sensitive personal and corporate data is not sufficiently protected, bad actors may take action. Consequences are often dramatic: the stolen data has a negative impact on the company’s reputation, which leads to cost loss, and the stolen information might be used for fraudulent acts. It is important to implement the best security practices and take into account all possible risks, including malware attachments, API threats, malicious code injection, phishing attacks, and others.
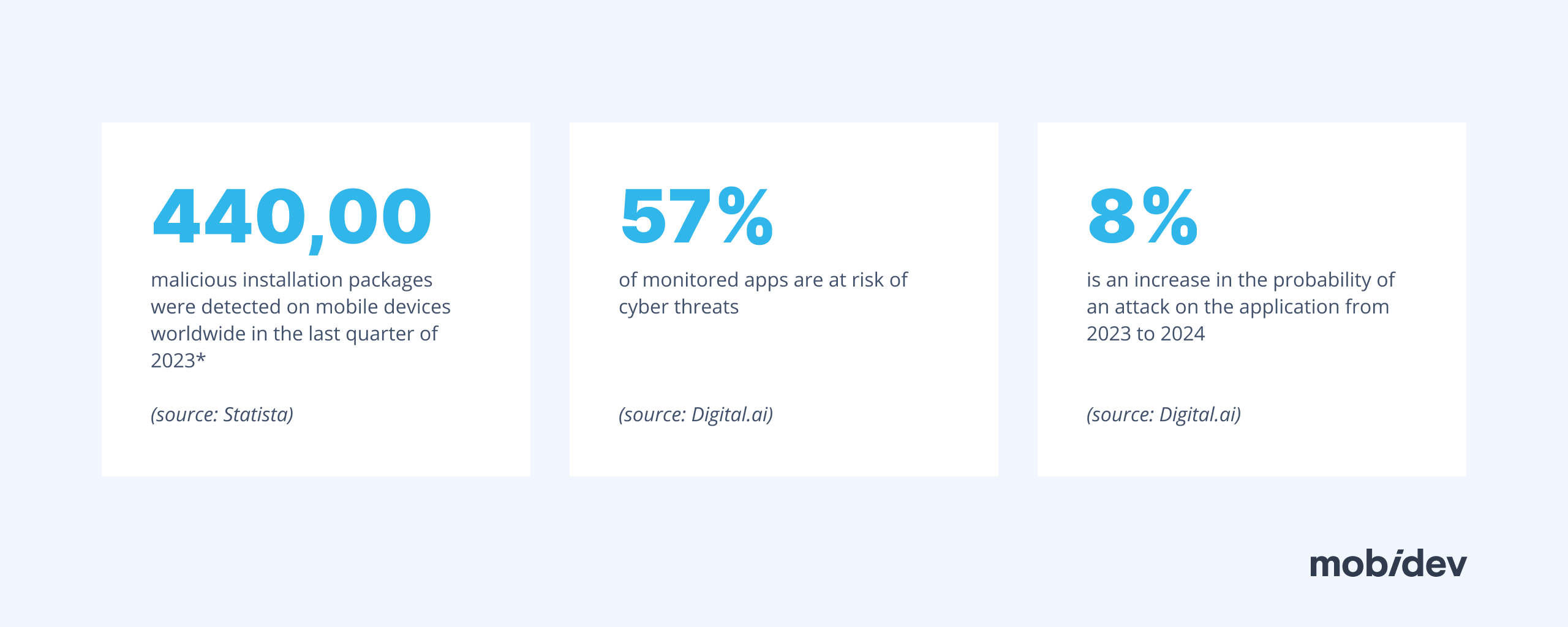
Statista reveals that the prevalence of mobile cyberattacks continues to grow. In 2022, 9% of all global cyberattacks were delivered via mobile devices. This trend continued into the last quarter of 2023, when approximately 440,000 malicious installation packages were detected on mobile devices worldwide.
Certain types of cyberattacks, such as smishing (SMS phishing) and vishing (voice phishing), are specifically designed to exploit the vulnerabilities unique to mobile devices. According to Lookout’s Q1 2025 Mobile Threat Landscape Report, there is a massive increase in social engineering and phishing attacks, including a nearly threefold rise in phishing, malicious, and offensive links delivered to mobile devices compared to the previous year.
Digital.ai’s recent study found that 57% of monitored apps are at risk of cyber threats, with Android apps being more vulnerable than their iOS counterparts. According to the study, 76% of Android apps are at potential risk compared to 55% of iOS apps.
As you see, the threat landscape is growing and it’s important to prioritize security for mobile applications when launching new or updating existing products. Let’s dive into the main risks to be neutralized.
The Key Mobile App Vulnerabilities and Threats
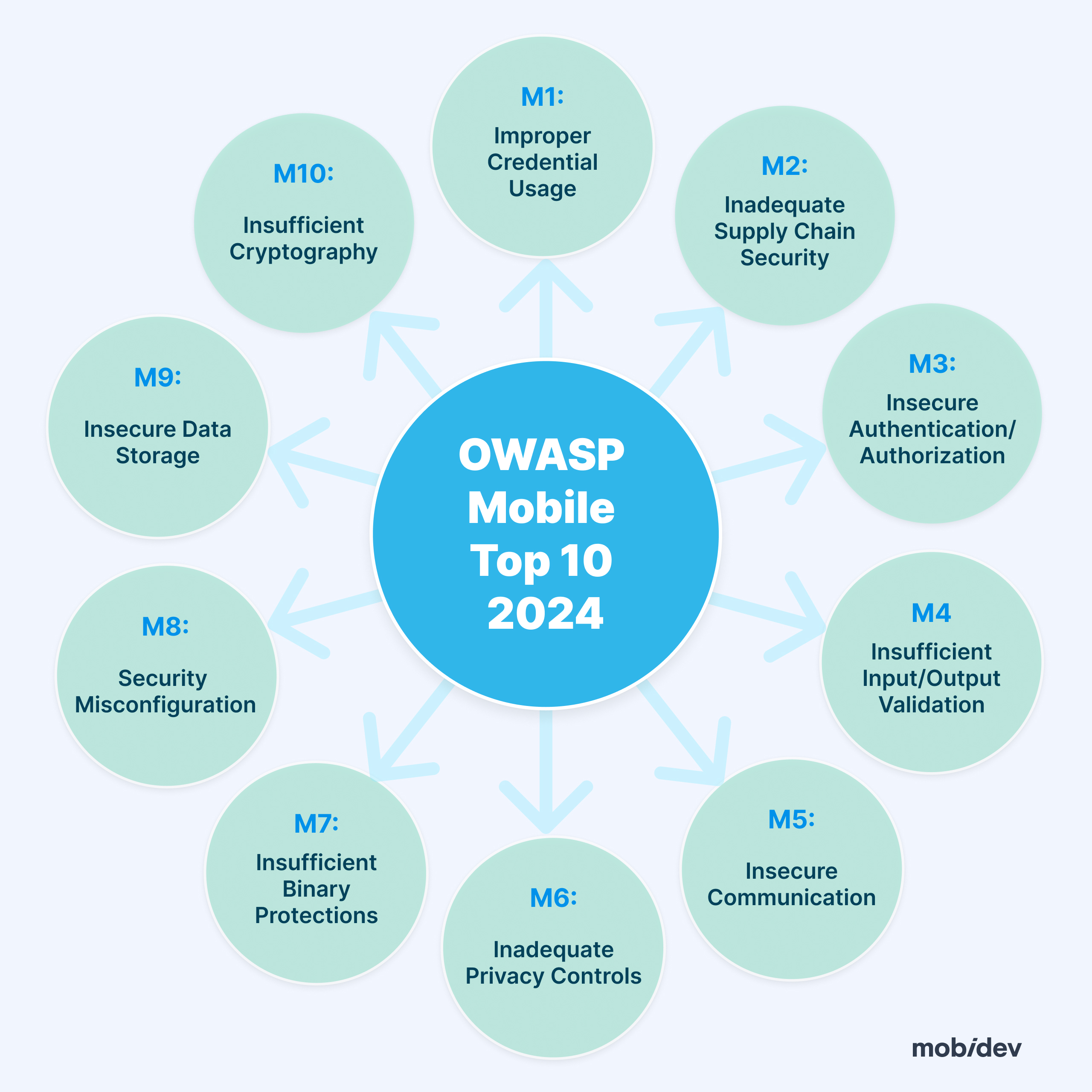
The OWASP Mobile Top 10 for 2024 identifies the most critical vulnerabilities affecting mobile apps today. These include the following:
- Improper Credential Usage. This vulnerability arises from poorly managed credentials, such as hardcoded passwords or storing sensitive information in plaintext. Such practices can lead to unauthorized access and potential data breaches.
- Inadequate Supply Chain Security. When third-party libraries or components are integrated into apps without thorough security checks, it opens the door for attackers to exploit these weak points and insert malicious code.
- Insecure Authentication/Authorization. Weak or flawed authentication processes can allow unauthorized users to gain access to restricted areas of an app, compromising sensitive information.
- Insufficient Input/Output Validation. Apps that do not properly validate user inputs and outputs are vulnerable to various attacks, including data manipulation and code injection, which can undermine the app’s functionality and security.
- Insecure Communication. If an app transmits sensitive data over unencrypted channels or uses weak encryption, that data is susceptible to interception, leading to privacy breaches and potential exploitation.
- Inadequate Privacy Controls. This risk arises when apps do not sufficiently protect user data, leading to unauthorized access and privacy violations, which can erode user trust.
- Insufficient Binary Protections. The lack of measures to protect the app’s binary code makes it easier for attackers to reverse engineer or tamper with the app, potentially leading to unauthorized modifications or data extraction.
- Security Misconfiguration. Poorly configured security settings, such as default passwords or unnecessary features, can make an app more vulnerable to attacks.
- Insecure Data Storage. Storing sensitive information in easily accessible locations on a device, or failing to encrypt data, leaves it exposed to potential breaches.
- Insufficient Cryptography. Using weak or improperly implemented cryptographic techniques can make sensitive data more vulnerable to attacks, compromising the app’s security and user privacy.
Combating these threats requires using the best practices and standards to minimize the attack surface area.
Mobile Application Security Standards and Best Practices
To enhance mobile app security, make sure to apply best practices while building or modernizing your application.
- Secure your code
Using secure coding practices, regularly reviewing and updating your code to address potential weaknesses, and considering code obfuscation techniques can make it harder for attackers to understand and reverse-engineer the code of a mobile app.
- Implement strong authentication
Strong passwords and multi-factor authentication (MFA) are key to improving security by preventing unauthorized access. Adding biometric authentication, like fingerprint or facial recognition, offers even more protection.
- Protect data
Encryption helps to maintain security, both during transmission and while storing data on a device. With secure protocols, such as HTTPS, network communication is protected from unauthorized access and interception.
- Regularly update and patch
Keeping the app and its components up-to-date with the latest security patches is essential. Using automated tools can help manage these updates and patches to maintain robust security.
- Conduct thorough security testing
Develop a clear testing strategy and regularly test your app for vulnerabilities using penetration testing and vulnerability scanning. This will help to identify weaknesses and locate exploitable flaws.
- Monitor for threats
Implementing real-time threat monitoring allows you to detect and respond to potential attacks promptly. The important role here is assigned to security analytics, patterns, and trends identification.
- Educate users
Users should be informed about best practices for protecting their accounts and devices, including using strong passwords and enabling multi-factor authentication. Clear guidelines should also be provided on how to report any suspicious activity to ensure swift response and enhanced security.
- Comply with security standards
Adherence to industry standards and regulations, such as GDPR, CCPA, and HIPAA, is essential for maintaining data security and privacy. Regular compliance audits guarantee that all practices align with these requirements.
Some other advice:
- It’s also important to use reliable third-party libraries and keep them updated to avoid vulnerabilities.
- Protect your APIs from unauthorized access by using strong authentication methods.
- When it comes to the network, it should be secure and regularly maintained to prevent attacks.
- Finally, have a solid backup plan in place to quickly recover from any data breaches.
Get a Free Mobile App Security Checklist
DownloadNavigating the Challenges of Secure Mobile Application Development
Security should be a fundamental consideration from the very beginning. This involves embedding security principles throughout the software development process to anticipate potential risks and design solutions that effectively mitigate threats. By implementing security from the start, you can create more resilient applications that are better equipped to withstand attacks.
Threat modeling and secure coding practices
One of the first steps is to conduct thorough threat modeling. The process relies on identifying potential vulnerabilities and risks, allowing developers to prioritize security measures that directly address these concerns. Secure coding practices include validating all user inputs to prevent injection attacks, such as SQL injection or cross-site scripting, and sanitizing data to remove potentially harmful code before it is processed or stored.
Secure authentication and third-party integrations
Implementing strong authentication mechanisms, like multi-factor authentication and secure password handling, ensures that only authorized users have access to sensitive information.
The overall security of the application heavily relies on libraries and frameworks. It is important to select components with a proven security record and that are regularly updated to address new vulnerabilities.
Architecture and data storage
A secure architecture that separates client and server components and enforces secure communication protocols helps protect sensitive data from unauthorized access. Proper data handling and secure storage practices that leverage platform-specific features like the iOS Keychain or Android Keystore are other critical aspects. Note that careful error handling and secure logging practices are necessary to prevent the accidental exposure of sensitive information and help monitor user activity for potential security threats.
Testing and auditing
Last but not least, is regular testing and auditing that will allow for maintaining a secure mobile application over time. Conducting code reviews with experienced developers helps identify security flaws early in the development process. Penetration testing can uncover vulnerabilities that could be exploited in real-world scenarios, while regular security audits ensure that the app’s security measures remain up-to-date and effective against emerging threats. This continuous attention to security helps safeguard the application and its users against the constantly evolving landscape of cybersecurity threats.
MobiDev Experience in Secure Mobile App Development
At MobiDev, we pay attention to the security of custom software product development. Let us share our experience to illustrate how reliable security mechanisms can contribute to a product’s success.
Case Study: Providing Security Measures for an AI-powered Mobile Application
Several years back, a fitness company [name is under NDA] contacted us for assistance in developing an iOS app with AI functionalities focused on tailoring workouts for users and maximizing workout efficiency. Since the app would process sensitive user data, prioritizing security was essential.
Our team incorporated top-notch security methodologies into the development process and implemented robust security mechanisms within the application to support the key functionality, build user trust, and enhance the brand’s reputation.
Security measures we implemented:
General:
As security measures are always about layering, we gradually added them to the app during the first version implementation, starting with basic must-have elements as part of the design and infrastructure setup:
- Secure connection with the server via HTTPS (even during development)
- Token-based authentication with short-lived access tokens
- Adherence to general policies, such as not storing credentials in code and restricting access to code.
These steps are easy to implement and they outline the essential minimum of safeguards.
Feature-related:
During the implementation of the functionality, we came across new scenarios that needed to be addressed from a security standpoint:
- On-device AI data processing: Data processing was carried out on-device without transmitting information to the server. This approach enhanced user privacy by keeping sensitive information local, making it more difficult for cyber threats to access user data.
- Data access control: We also implemented strict access controls to user personal data. This includes access to uploaded assets with a temporary link that is dynamically generated upon request and caching them locally to reduce bandwidth usage. Additionally, access restrictions at the application level ensure that only authorized users can access this data.
- Input validation: To prevent the submission of invalid or harmful data to the server, we implemented input validation on both the mobile client and server sides. Additionally, we established a clear response format that the mobile app expects. If there is any inconsistency, the app considers it invalid, preventing it from processing potentially malformed data.
As a client-side measure for handling user data, we have adopted two strategies:
– Securely store minimal data, such as an access token that is updated regularly
– Locally cache personal data and periodically invalidate this cache
This enabled us to avoid implementing more extensive security measures, such as additional encryption.
- App functionality protection: To protect the implementation details of valuable functionality from external access, we added an encryption layer on top of the data received from the server. This ensures that no sensitive information can be exposed through APIs, making it impossible to glean any insights about the data or its intended use from the raw JSON response. This approach is part of a broader security strategy that aims to limit what can be learned about the system’s internals through public interfaces.
- Third-party dependencies minimalization: By minimizing the number of dependencies and leaving only those we can be sure of, we have reduced the risks of third-party code introducing a vulnerability into our application.
Outcomes
In summary, we have adopted an approach that targets well-known security vulnerabilities and emphasizes the careful design of specific components, enabling us to effectively assess the system’s security status. The app was successfully deployed and launched and now its user base keeps growing.
Enable Secure Mobile App Development With MobiDev
At MobiDev, we prioritize security at every stage of the custom software development process, integrating it into the Secure Software Development Lifecycle (SSDLC). All the phases, from initial requirements gathering to final deployment, are infused with security measures to mitigate potential risks. By transforming the standard SDLC into an SSDLC, the MobiDev team emphasizes risk assessment, threat modeling, and regular security reviews to protect client applications from vulnerabilities.
A key component of MobiDev’s strategy is the use of Continuous Integration and Continuous Delivery (CI/CD) pipelines, which automate testing and deployment processes. The automation helps detect security issues early, allows for consistent application of security patches, and prevents the deployment of insecure code. Moreover, our in-house DevOps team configures and manages these pipelines, reinforcing security through regular checks and updates.
With 15 years in mobile app development services, the MobiDev team has developed its own approach to technical measures, robust authentication and access control methods, including multi-factor authentication (MFA) and biometric verification, and the application of APIs.
Feel free to contact us to discuss how our expertise could serve your business needs.