Contents:
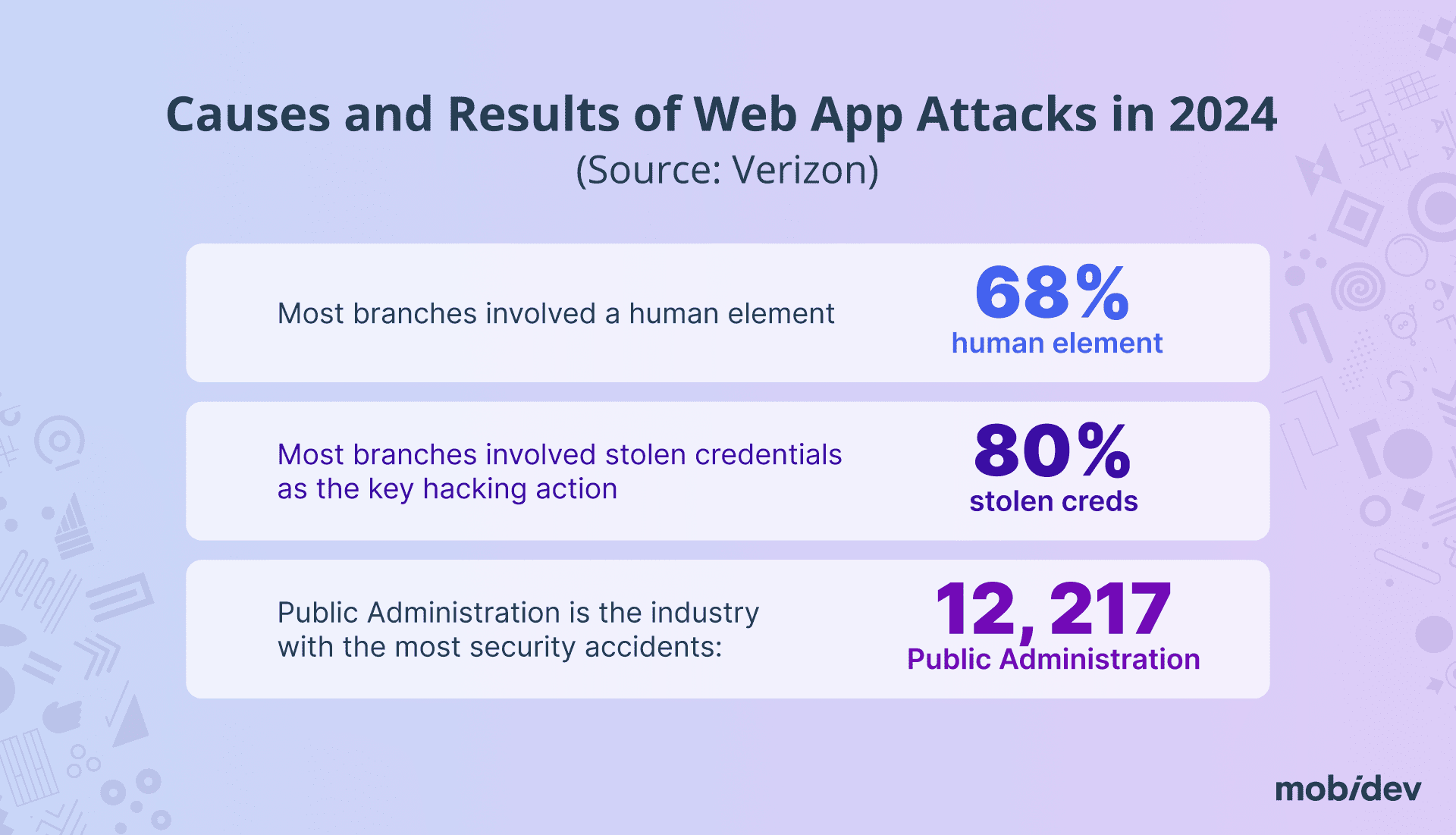
Over the past years, many organizations have transitioned to remote work using cloud-based enterprise systems, forcing application security teams to quickly adapt to changing usage patterns and an increasing array of challenges. Due to their exposure to the Internet, web applications are particularly vulnerable compared to other IT assets. Many attacks against web applications focus on manipulating user inputs via web forms, and machine inputs via APIs.
This article is aimed to help product owners and tech leaders like you navigate the complexities of securing web applications. I’ll delve into common vulnerabilities, share best practices for strengthening the security of your web application against malicious attacks, and provide a list of actionable steps you can take to prevent accidental damage. By following the guidance in this article, you can better protect your organization’s digital assets and minimize the risk of costly breaches.
Understanding the importance of securing your web application
As the digital world continues to expand and develop, the threat of cyberattacks grows alongside it. Hackers are becoming increasingly sophisticated, targeting web applications with greater frequency and precision. The consequences of a successful attack can be devastating; from significant financial losses and reputation damage to severe operational disruptions.
For businesses, especially those that handle sensitive data, investing in reliable security mechanisms is not just a precaution, but a necessity. Without robust security, the risks include data breaches, loss of customer trust, and compliance violations, which can all significantly impact a company’s success.
The list of the key web application vulnerabilities and threats
Web application vulnerabilities are security weaknesses that attackers exploit to manipulate source code, gain unauthorized access, steal data, or disrupt the application’s functionality. The OWASP Top 10 list identifies the most critical security risks for web applications. Here’s a brief overview of each:
- Broken access control — when access control is poorly implemented, unauthorized users can gain access to sensitive data or systems, leading to data breaches or privilege escalation.
- Cryptographic failures — weak encryption practices can expose sensitive data. This includes using outdated algorithms or improper key management, which can lead to data leakage.
- Injection — attackers inject malicious code, such as SQL, to manipulate databases, extract data, or gain unauthorized administrative access.
- Insecure design — flaws in the application design that lead to vulnerabilities, exposing the system to various threats from the outset.
- Security misconfiguration — improperly configured security settings, such as leaving unnecessary features enabled, can allow attackers to exploit the system.
- Vulnerable and outdated components — using outdated or insecure third-party libraries and frameworks can introduce vulnerabilities that attackers can exploit.
- Identification and authentication failures — inefficient authentication mechanisms, like insufficient password policies, can lead to unauthorized access.
- Software and data integrity failures — this occurs when software updates, critical data, or CI/CD pipelines are tampered with, leading to compromised systems.
- Security logging and monitoring failures — insufficient logging and monitoring make it difficult to detect and respond to breaches, allowing attackers to exploit systems undetected.
- Server-Side Request Forgery (SSRF) — attackers manipulate a server to make unauthorized requests, potentially exposing internal systems or leading to data exfiltration.
To mitigate these risks, it is crucial to adopt secure coding practices, sanitize inputs and outputs, and conduct regular security testing throughout the web application development lifecycle. Additionally, continuous monitoring and scanning of third-party components are essential to detect and fix vulnerabilities quickly. In the following sections, I’ll explain how to do it effectively.
Web application security techniques and tools
The most powerful security technique in web development is to think about security in all, even smallest, details. Web application security is about not just the code base, but also about project processes, data storing, company policies, etc. In the end, it doesn’t matter how good and protected your code is, if you have your API documentation publicly available, or the super admin password written on a whiteboard in the office.
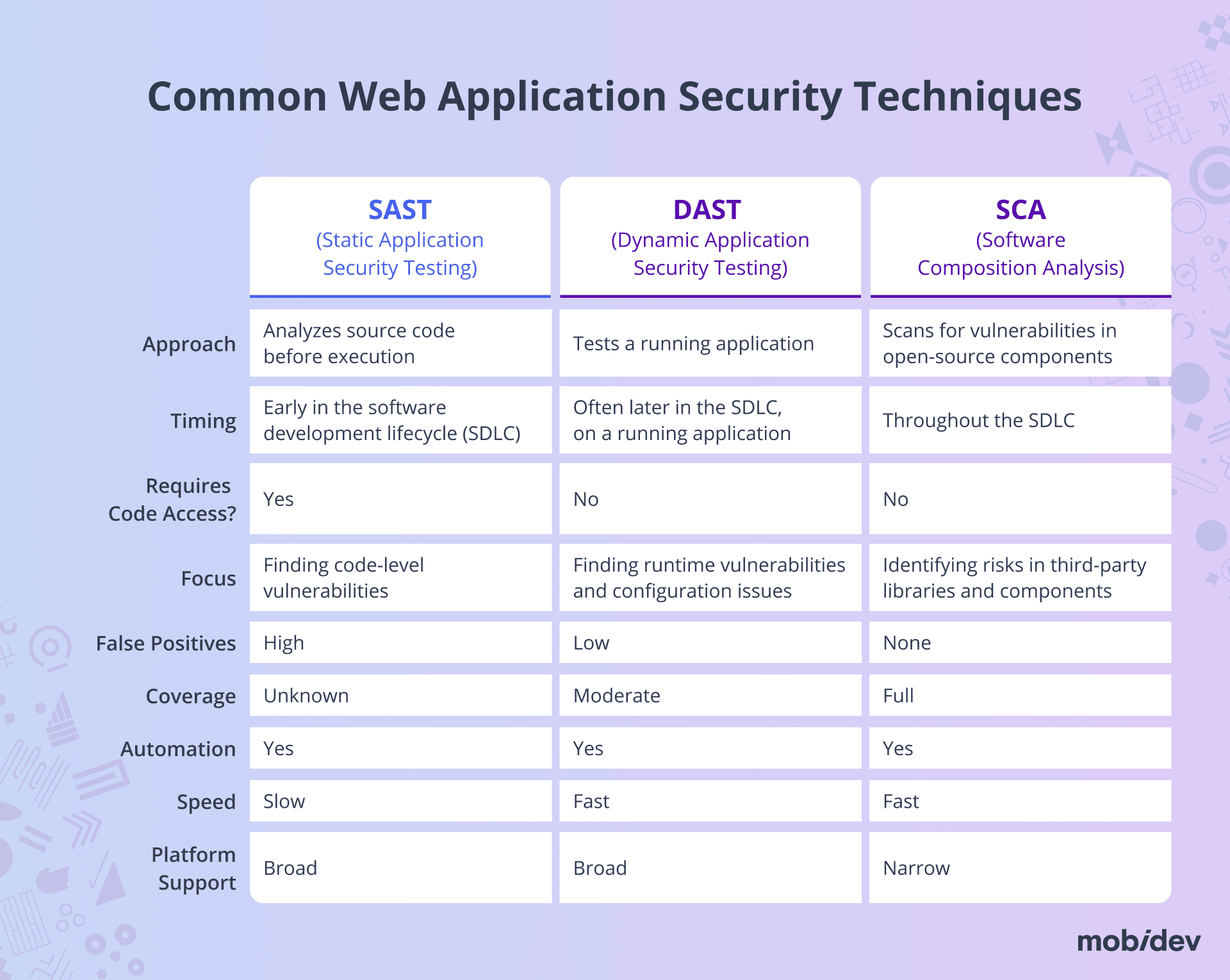
Ensuring security in web applications starts with a solid foundation in project security. Even with flawless processes, continuous vigilance is essential. Two primary methods for securing web applications are static and dynamic security testing. These methods are complementary and should be used together for comprehensive protection.
1. Static Application Security Testing (SAST)
SAST solutions analyze your source code to identify vulnerabilities and security risks. This type of scanning is typically integrated at multiple stages of development, particularly when new code is committed to the codebase or during the build process.
As SAST is rule-based, it may produce false positives, necessitating careful analysis to identify genuine security concerns.
Recommendation from MobiDev’s experience:
We use SonarQube for static analysis to monitor security issues during development. Integrating SonarQube with your CI/CD pipeline ensures that every commit or merge is scanned. SonarQube not only addresses security but also checks code maintainability and reliability. Supporting over 20 programming languages, it’s compatible with most frontend and backend frameworks.
2. Dynamic Application Security Testing (DAST)
DAST involves testing live or running applications to uncover vulnerabilities. This can be performed both manually and automatically using specialized tools.
Manual testing involves interacting with the application’s API using tools like Burp Suite, Fiddler, or Postman. Automated DAST tools, on the other hand, send numerous requests, including unexpected or malicious inputs, to the application, analyzing the results for security weaknesses.
Recommendation from MobiDev’s experience:
Following a thorough manual security analysis, we used OWASP ZAP, an open-source web application security scanner, to expedite regression testing. While scanners can’t match human creativity, root cause analysis, or out-of-the-box thinking, they excel at handling repetitive tasks quickly and at scale.
3. Penetration Testing
Penetration testing is a comprehensive security technique that combines dynamic scanning tools with human expertise to uncover vulnerabilities in a web application’s security.
Penetration testers simulate real-world attacks by exploiting vulnerabilities, gaining unauthorized access, stealing data, and disrupting services. This testing is done under a contract with the application owner, within a defined scope, and without causing real harm to the organization.
Although more complex than SAST and DAST, penetration testing can reveal additional risks that automated tools might miss.
4. eXtended Detection and Response (XDR)
XDR platforms represent a new generation of security solutions, providing security teams with a unified interface to detect and respond to threats across the entire IT environment.
XDR collects security data from all layers of the stack, including web applications, networks, clouds, and endpoints. It leverages advanced analytics and automation to detect both known and unknown threats. Most importantly, XDR integrates directly with security tools, enabling real-time threat response.
Top 8 Best Practices for Securing Web Applications
Securing web applications requires a multi-layered approach that addresses evolving security threats and leverages the latest best practices. Here are the key 8 strategies to ensure your web application remain secure.
- Adopt a cybersecurity framework
- Set up authentication and access control
- Prevent security misconfigurations
- Secure use of open-source components
- Adopt exception management
- Adhere to container security best practices
- Adopt quality assurance and security testing
- Incorporate security into CI/CD process
Let’s dive into exploring each of the strategy in details.
1. Adopt a cybersecurity framework
Rather than building a framework from scratch, consider leveraging established industry-standard frameworks to guide your cybersecurity efforts:
- ISO 27001: Provides comprehensive guidelines for establishing, maintaining, and continually improving an Information Security Management System (ISMS), helping organizations manage sensitive data effectively.
- NIST: Developed by the U.S. National Institute of Standards and Technology, this framework is the most widely adopted in large organizations for comprehensive cybersecurity planning and risk management.
- CIS Controls: Created by the Center for Internet Security (CIS), this framework outlines a set of best practices for effective cyber defense, specifically designed to protect against common cybersecurity threats.
- ASVS: The Application Security Verification Standard (ASVS) offers a foundation for testing the security controls of web applications and provides a detailed list of requirements to ensure secure development practices.
By regularly reviewing and updating your policies and processes in line with these frameworks, you can enhance your organization’s overall security strategy.
2. Set up authentication and access control
Ensuring robust authentication and access control remains critical, yet many web applications still overlook fundamental measures. Adhering to the following principles is essential:
- Implement strong password policies: Adopt effective password policies, including secure password recovery processes. Set policies for password expiration and rotation, and prioritize the use of multi-factor authentication (MFA) to mitigate the risks associated with compromised credentials.
- Mandate re-authentication for sensitive actions: Require users to re-authenticate when accessing sensitive features or conducting transactions, adding an extra layer of security.
- Principle of Least Privilege (POLP): Assign users only the permissions necessary to perform their roles, minimizing the potential damage from compromised accounts.
- Comprehensive encryption: Ensure that all passwords and credentials are encrypted both at rest and in transit using secure protocols like SSL/TLS.
- Monitor and respond to suspicious activity: Continuously monitor user accounts for anomalous behavior, such as unusual login patterns or access attempts, and take appropriate actions like locking accounts or prompting password changes.
- Implement AI authentication: AI-driven biometric verification, like facial or voice recognition, offers enhanced accuracy, minimizes reliance on passwords, and provides a seamless, user-friendly experience while safeguarding sensitive data.
3. Prevent security misconfigurations
Security misconfigurations are a common and often preventable source of vulnerabilities in web applications. To mitigate this risk:
- Secure administrator accounts: Always set strong passwords for administrator accounts and change default usernames to reduce the risk of unauthorized access.
- Protect sensitive files and directories: Use configuration management tools to secure files and directories containing sensitive information.
- Close unnecessary ports: Regularly audit open ports and close any that are not essential for your application, reducing the attack surface.
- Keep software up to date: Regularly update all software libraries, plugins, and frameworks to their latest stable versions to protect against known vulnerabilities.
- Continuous vulnerability scanning: Implement automated tools to scan your software packages for security vulnerabilities on a regular basis.
- Adopt secure communication protocols: Ensure that all communication between users and your application is encrypted and that digital certificates are kept up to date.
4. Secure use of open-source components
The widespread use of open-source components in custom software development introduces significant security challenges. With 99% of applications incorporating open-source elements, it’s important to:
- Assess the security of open-source components particularly in industries such as Retail, Healthcare, and Education, where the use of open-source has surged, increasing the number of vulnerabilities.
- Monitor for vulnerabilities in open-source components, and update them promptly to mitigate security risks.
5. Adopt exception management
Exception handling is often an overlooked aspect of web application security, that’s why it is critical to:
- Hide stack traces from users: Ensure that exceptions do not expose stack traces or other detailed error information to users, as this information can be leveraged by attackers.
- Plan for all scenarios: Design your application to handle both “happy” and “unhappy” paths of user operations. Properly anticipate and manage potential errors with meaningful exception handling, preventing attackers from exploiting edge cases.
6. Adhere to container security best practices
As containerization continues to grow in popularity, securing containerized environments is paramount:
- Use trusted base images: Always start with trusted base images and conduct vulnerability scans on these images, including those you create yourself.
- Handle secrets securely: Avoid embedding sensitive information such as credentials directly within container images. Instead, use secret management mechanisms provided by platforms like Docker or Kubernetes.
- Avoid granting root access: Prevent containers from running with root privileges, as this can lead to system-wide compromise if the container is breached. Always define a non-root user in your images and avoid using privileged containers.
- Adopt network segmentation: Restrict containers’ network access to only what is necessary. Place containers in protected subnets and minimize exposure to the internet unless absolutely required.
Recommendation from MobiDev’s experience:
Utilize services like Amazon Elastic Container Registry (ECR) that provide built-in security scans for Docker images, enabling you to detect potential security issues early.
7. Adopt quality assurance and security testing
Comprehensive security testing is essential for maintaining the integrity of your web application. Best practices include:
- Combine SAST and DAST: Use Static Application Security Testing (SAST) to identify vulnerabilities during development and Dynamic Application Security Testing (DAST) to catch issues in the running application.
- Leverage penetration testing: Employ penetration testing, either as a service (PTaaS) for lightweight testing or full-scale testing by certified ethical hackers for more extensive applications.
- Ensure regulatory compliance: Stay informed about applicable regulations like GDPR, HIPAA, and PCI/DSS, and implement necessary compliance measures within your security framework.
8. Incorporate security into CI/CD process
Adopt continuous integration and continuous deployment (CI/CD) practices where each code update undergoes automated security testing and secure deployment. This ensures that security vulnerabilities are not introduced during deployment.
In a typical CI/CD deployment process, the following steps are critical:
- Source code scanning: Check code for style violations and security issues.
- Third-party library analysis: Scan all third-party libraries for vulnerabilities.
- Automated testing: Run unit tests to ensure code integrity.
- Secure deployment: Deploy new Docker images with all sensitive credentials stored securely, ensuring the deployment is halted if any security checks fail.
By sticking to these advanced security techniques, you can significantly enhance the resilience of your web applications in 2025 and beyond.
WEB APPLICATION SECURITY CHECKLIST
Get a free checklist to reduce the chance of forgetting important steps
DownloadMobiDev Success Story: Developing an Enterprise Verification-as-a-Service Solution
In 2007, a US-based company began developing an enterprise verification-as-a-service (EVaaS) platform to address the growing issue of password-related breaches. They envisioned a microservice-based single sign-on (SSO) solution utilizing biometric authentication via face and voice recognition. MobiDev took full ownership of transforming this vision into a secure, scalable product.
How we delivered:
- Conducted a detailed business analysis and finalized the product vision, requirements, and design assets. Our team also performed machine learning research, reviewing datasets, recommending algorithms, and defining the app development roadmap, ensuring a secure tech stack that fits the project’s specific needs.
- Identified optimal datasets for voice and facial recognition and evaluated over 10 OCR solutions for validating US driver’s licenses and passports, ultimately integrating Google Vision for optimal accuracy.
- Implemented a microservice architecture to allow flexibility and scalability, leveraging WebRTC for processing media data, and supporting the core functionalities of face and voice recognition.
- Implemented enhanced security features. As the software is web-based, it operates on both smartphones and most computers equipped with cameras and audio capabilities. Unlike mobile apps, this web application cannot fully utilize the extended identity verification features native to smartphones. To address this, the MobiDev team collaborated with the client to overcome these limitations by implementing supplementary services. These included liveness detection techniques, such as prompts for users to smile or blink, along with anti-spoofing measures to protect against presentation attacks, ensuring secure and reliable authentication.
Business Outcomes:
The EVaaS solution delivered enhanced security through biometric verification, significantly reducing the risk of breaches tied to weak or stolen passwords. With integrated advanced security measures like face anti-spoofing and multi-layered biometric authentication, the platform now provides secure access to sensitive data across sectors like healthcare, insurance, and banking. As a result, it meets stringent industry compliance standards, offering robust protection against modern security threats.

View the full success story:
DEVELOPING AN ENTERPRISE VERIFICATION-AS-A-SERVICE SOLUTIONHow MobiDev Ensures Web Application Security
At MobiDev, we are committed to staying ahead of emerging threats and continuously enhancing our security practices. We integrate security into every stage of the development lifecycle, adopting a “security by design” approach. This ensures that vulnerabilities are identified and mitigated early, reducing the risk of breaches post-deployment. Our team keeps pace with the latest security tools and techniques, ensuring that our clients benefit from cutting-edge solutions for web application development services.
As experts in leading cloud platforms like Google Cloud, Azure, and AWS, we ensure that your applications are built with robust cloud security measures, protecting your data and operations in the cloud environment. MobiDev also has extensive experience with key compliance standards such as GDPR, CCPA, HIPAA, GLBA, and PCI DSS. We help our clients navigate these complex regulations, ensuring that their web applications meet all necessary security and legal requirements.
By working with MobiDev, you can trust that your web applications will be secure, compliant, and resilient against external threats. Contact us to discuss how we can help safeguard your web applications and provide the peace of mind you need to focus on your core business.
Download the 1-page MobiDev web development offer to make sure you can stay connected with us
Web App Development Offer